Can AI Help Automate Threat Modeling? Yes, When Done Right
Click to enlarge
The cybersecurity landscape is evolving rapidly, and with it comes the pressing question: Can artificial intelligence truly help automate the complex process of threat modeling? The answer is a resounding yes – but only when implemented with the right approach, clear structure, and proper context.
The Current State of Threat Modeling
Traditional threat modeling is a time-intensive process that requires deep security expertise. Security professionals must analyze system architectures, identify potential vulnerabilities, map attack vectors, and prioritize risks – all while keeping up with evolving threat landscapes and new attack techniques.
This manual approach, while thorough, faces several challenges:
- Time constraints limiting comprehensive analysis
- Inconsistency across different security professionals
- Difficulty keeping pace with emerging threats
- Knowledge gaps in specialized attack techniques
- Scalability issues for complex systems
How AI Enhances the Threat Modeling Workflow
Let me walk you through a typical threat modeling session using AI-powered tools, demonstrating how artificial intelligence augments each step of the process.
Step 1: Creating Your System Architecture
The foundation of effective threat modeling starts with a clear representation of your system. You have three main approaches:
Manual Diagram Creation
Using the visual editor, you drag and drop components from a library of 150+ security-focused nodes including firewalls, AI gateways, SCADA systems, and cloud services. Components snap to a grid for clean alignment, and you can organize them into 35 different security zones like DMZ, Internal Network, Cloud, or Zero Trust environments.
Click to enlarge
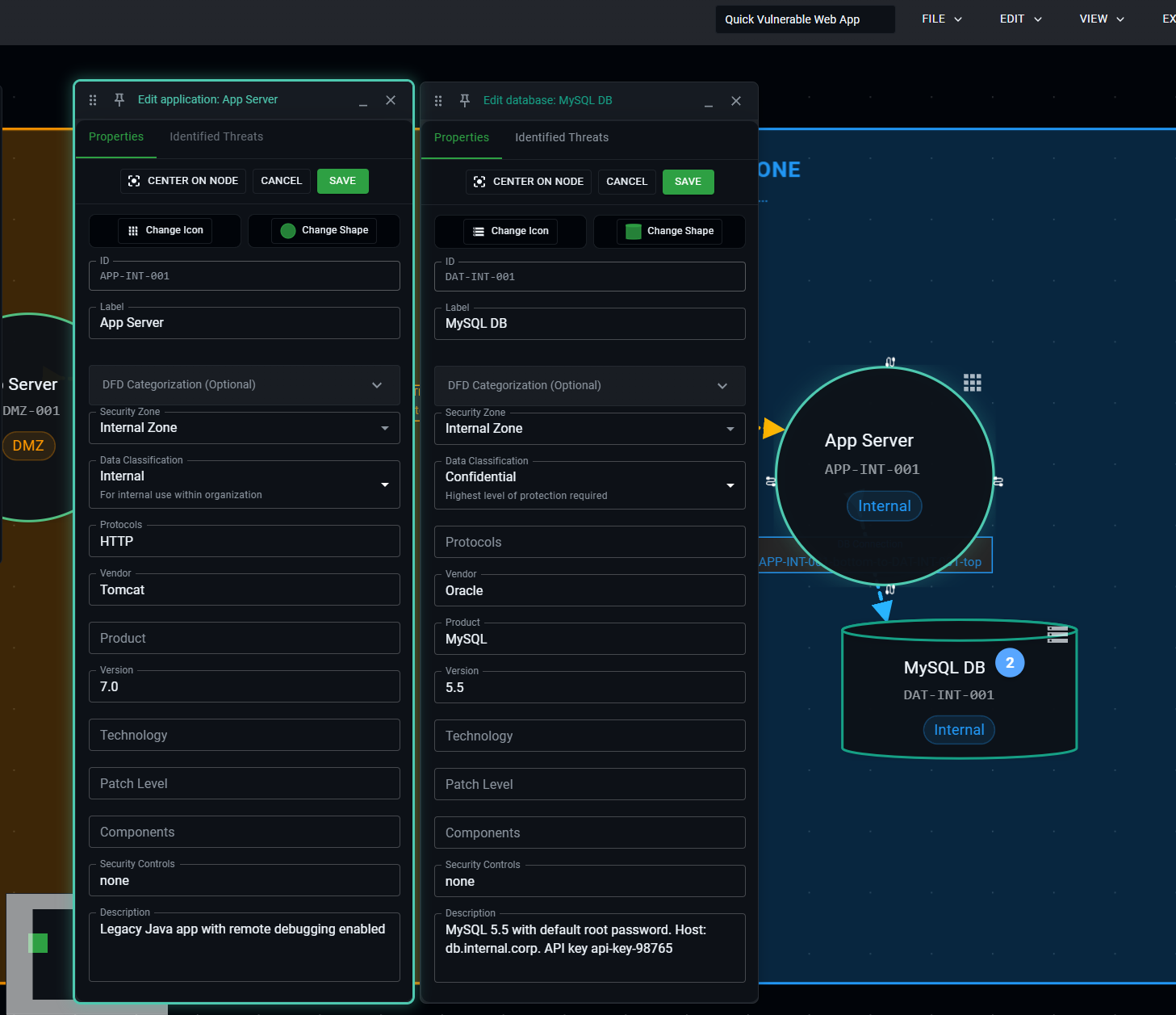
Each component can be enriched with contextual information that helps the AI provide more accurate and specific threat analysis. Simply double-click any node or edge connection to open the editor and add details like:
- Component purpose and functionality
- Data sensitivity levels and classification
- Authentication mechanisms and access controls
- Network protocols and communication patterns
- Dependencies and integration points
- Existing security controls and configurations
Click to enlarge
This contextual information becomes part of the AI's knowledge base when analyzing your system, enabling it to provide highly specific recommendations based on your actual implementation details rather than generic security advice.
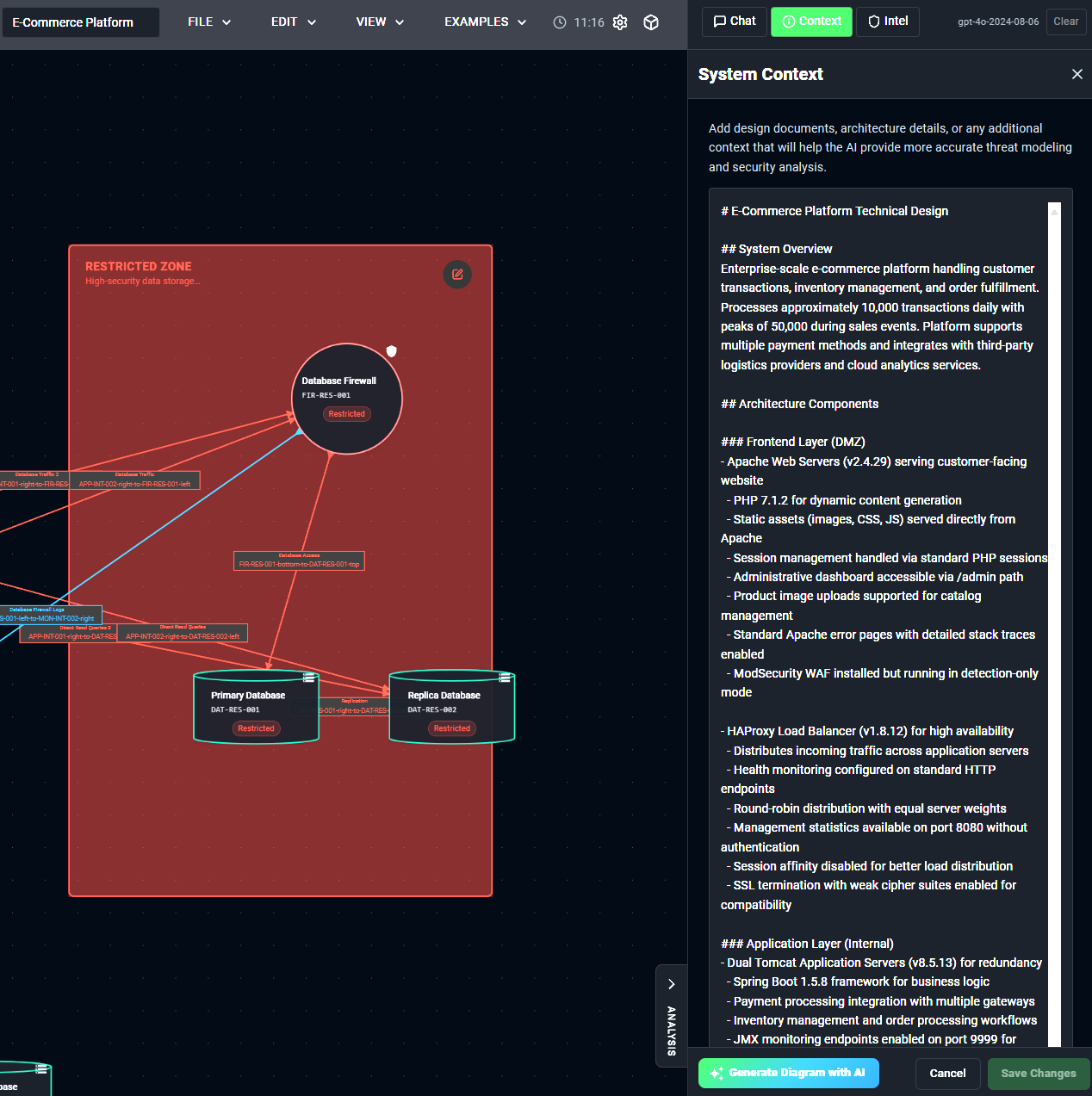
Custom Context Panel
Beyond individual component details, the custom context panel allows you to provide comprehensive system and business context that shapes the AI's analysis. This is where you can add:
- Overall system architecture and design decisions
- Business requirements and compliance needs
- Existing security policies and procedures
- Known vulnerabilities or areas of concern
- Technology stack and framework details
- Performance requirements and constraints
Click to enlarge
This system-wide context ensures the AI understands not just the technical architecture but also the business environment, compliance requirements, and operational constraints that influence security decisions.
Threat Intelligence Import
Stay ahead of emerging threats by importing threat intelligence directly into your analysis. The threat intel context panel accepts multiple standard formats and automatically parses relevant information based on your system architecture:
- STIX 2.1 bundles for structured threat data
- MISP event exports with indicators of compromise
- CSV/JSON feeds from threat intelligence platforms
- PDF reports from security vendors (AI-parsed)
- YARA rules and detection signatures
- Custom threat briefings and advisories
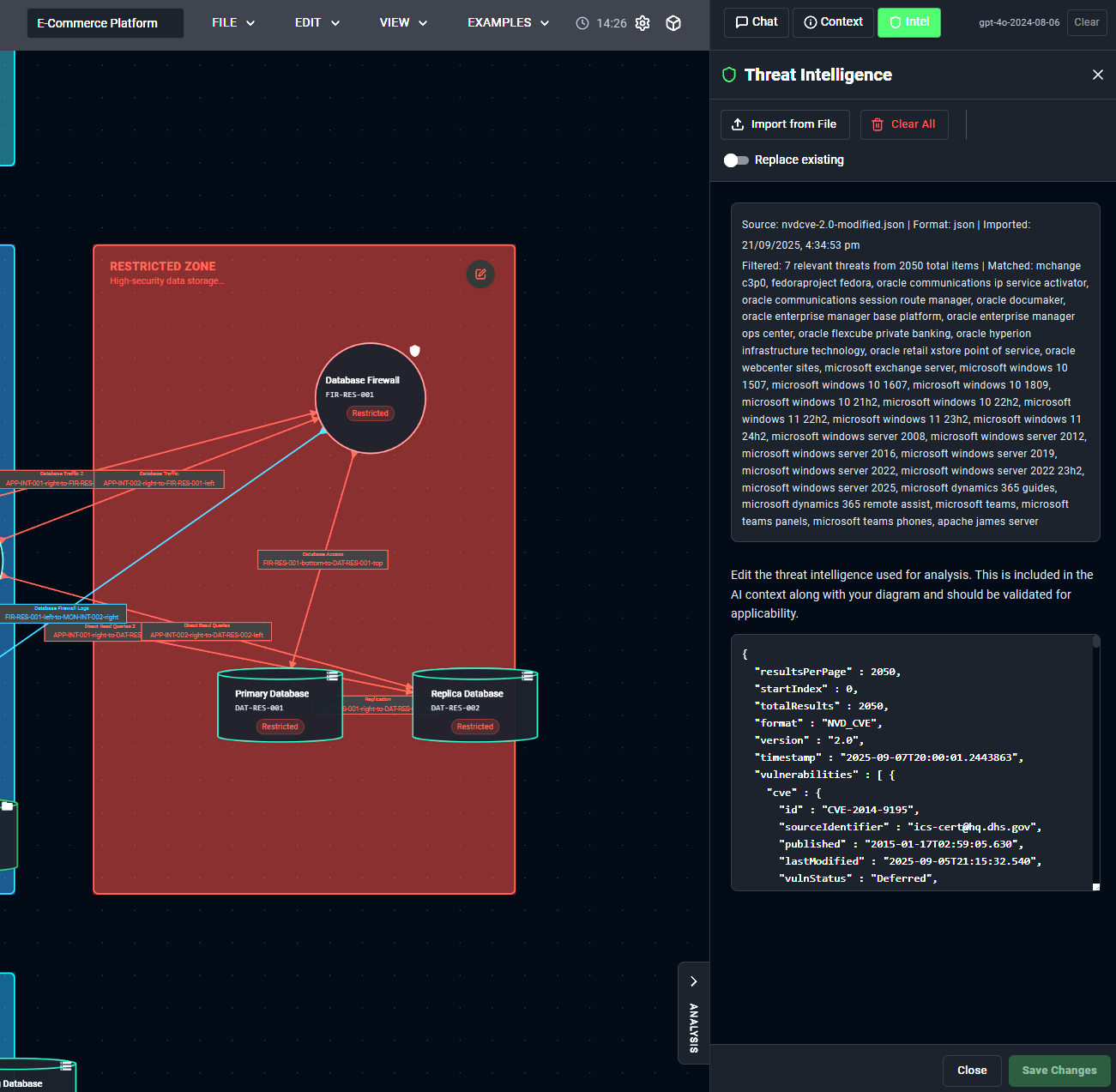
Click to enlarge
The AI intelligently extracts relevant threats, vulnerabilities, and attack patterns from your imported intelligence, correlating them with your specific architecture. This means you get targeted analysis based on real-world threats that actually apply to your technology stack and deployment model.
Import Existing Diagrams
Already have architecture diagrams? Import them directly from popular formats:
- Mermaid diagrams
- DrawIO/diagrams.net files
- PlantUML specifications
- Graphviz DOT files
- JSON structured data
AI-Generated Diagrams
Describe your system in plain language using the custom context panel, and the AI will generate a reasonably accurate threat model diagram based on your description. For example:
"Create a threat model for a web application with React frontend, Node.js API, PostgreSQL database, Redis cache, all deployed on AWS with CloudFront CDN, ALB, and RDS in private subnets."
The AI interprets your description and creates a visual representation with appropriate components and connections based on what you've specified in the context.
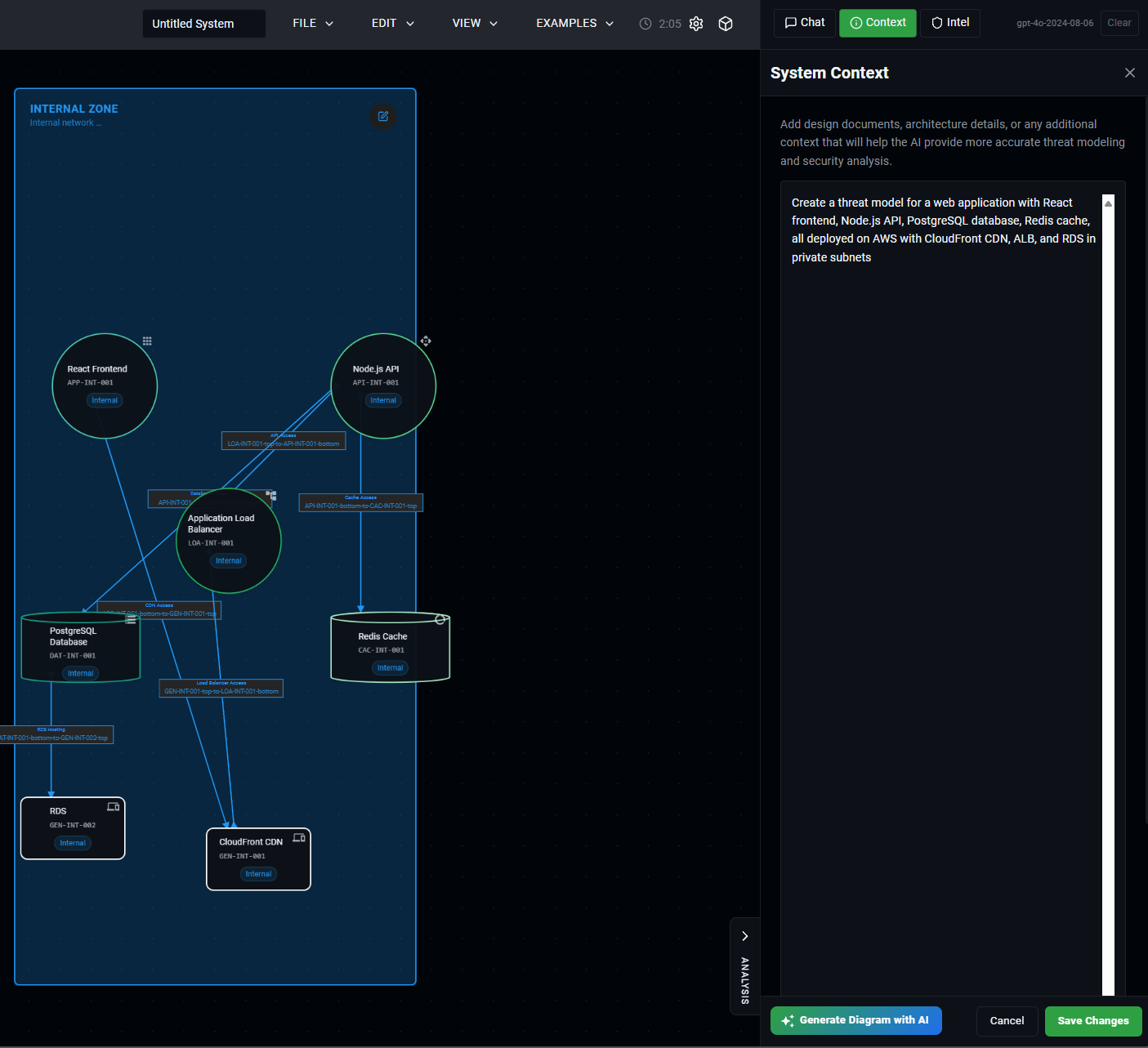
Click to enlarge
Step 2: Interactive AI Analysis
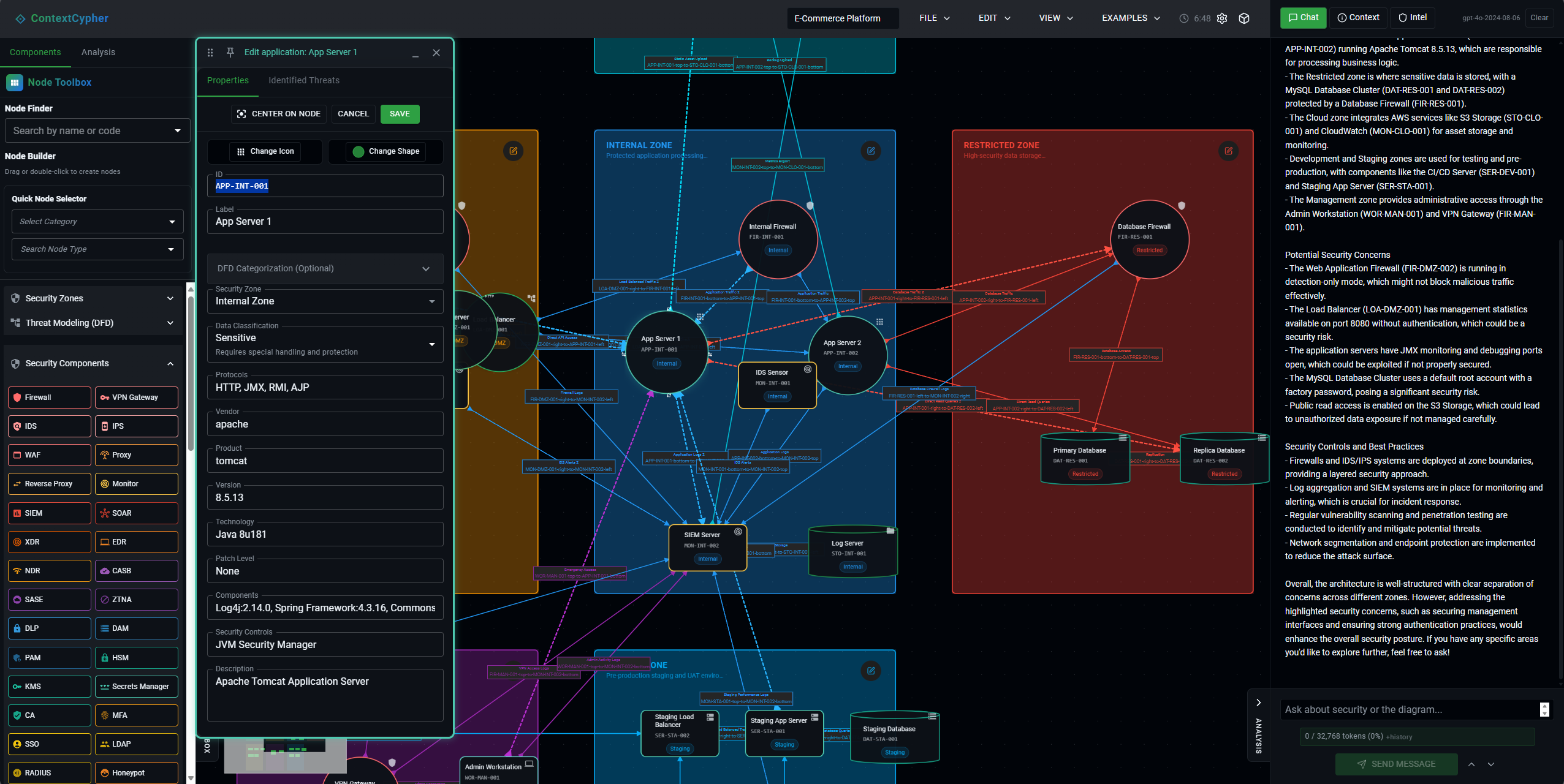
Once your architecture is in place, the AI assistant becomes your security analysis partner. The chat interface allows natural conversation about your system's security posture.
Conversational Threat Analysis
You can ask specific questions about your architecture:
You:
"What are the main attack vectors for the web application component?"
AI Assistant:
"Based on your architecture, I've identified several attack vectors for the web application: 1. Cross-Site Scripting (XSS) through user input fields 2. SQL Injection if input validation is insufficient 3. Session hijacking through insecure cookie handling 4. API abuse through the exposed endpoints..."
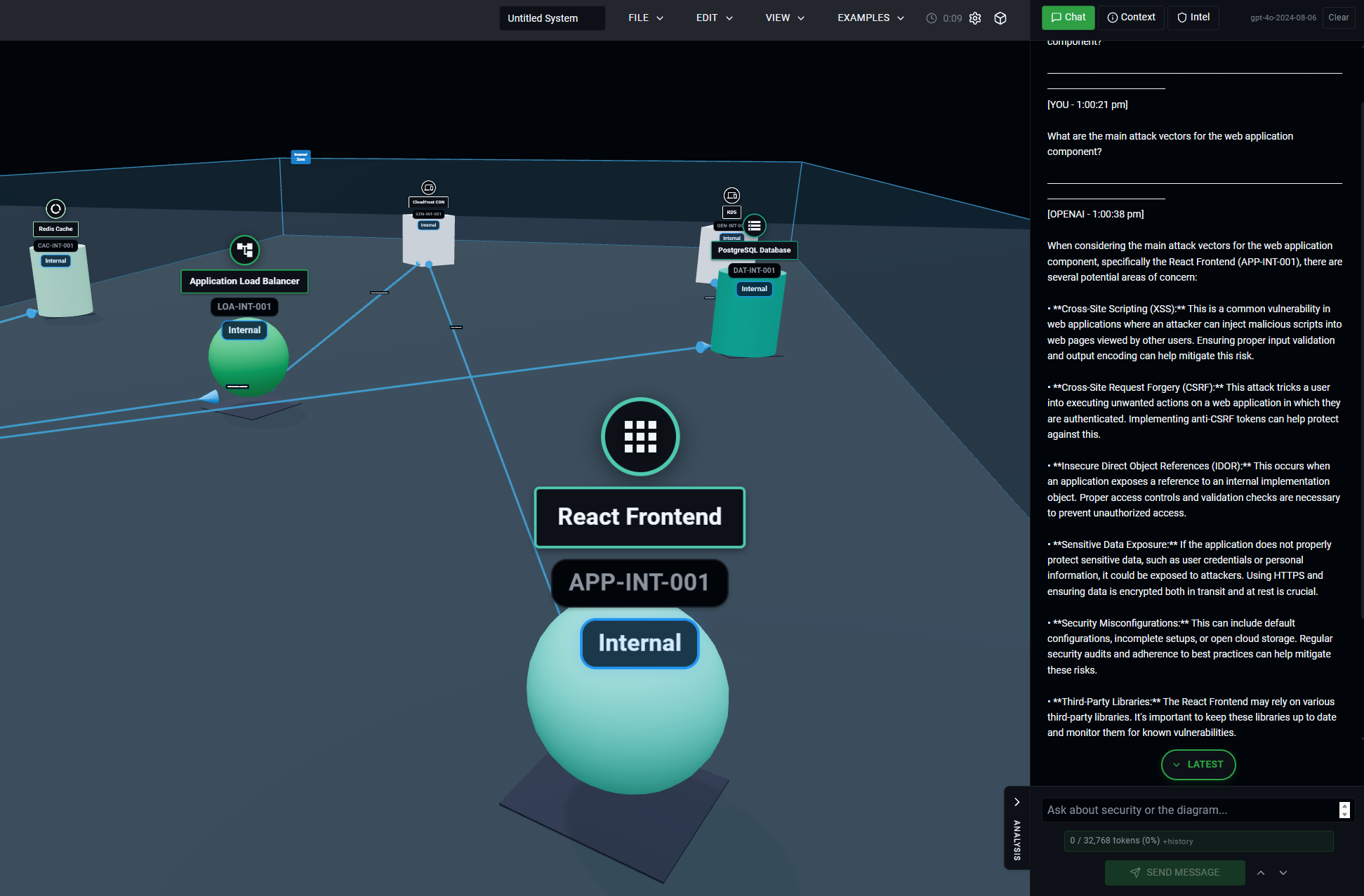
Click to enlarge
Component-Specific Analysis
Simply reference any component by its name or unique index code (like APP-INT-001 or FIR-RES-001) in your question, and the AI will provide targeted analysis for that specific component. The AI understands the complete diagram structure and can provide targeted threats based on:
- Component type and function
- Network position and exposure
- Connected systems and data flows
- Security zone placement
Step 3: 3D Security Visualization
Transform your 2D diagram into a fully navigable 3D environment with fly-around controls similar to Unreal Engine. You can freely navigate through your architecture, zoom in on specific areas, and view connections from any angle. The 3D view helps you:
- Identify overlooked connections between components
- Visualize network segmentation and security boundaries
- Understand data flow paths in complex architectures
- Present security architecture to non-technical stakeholders
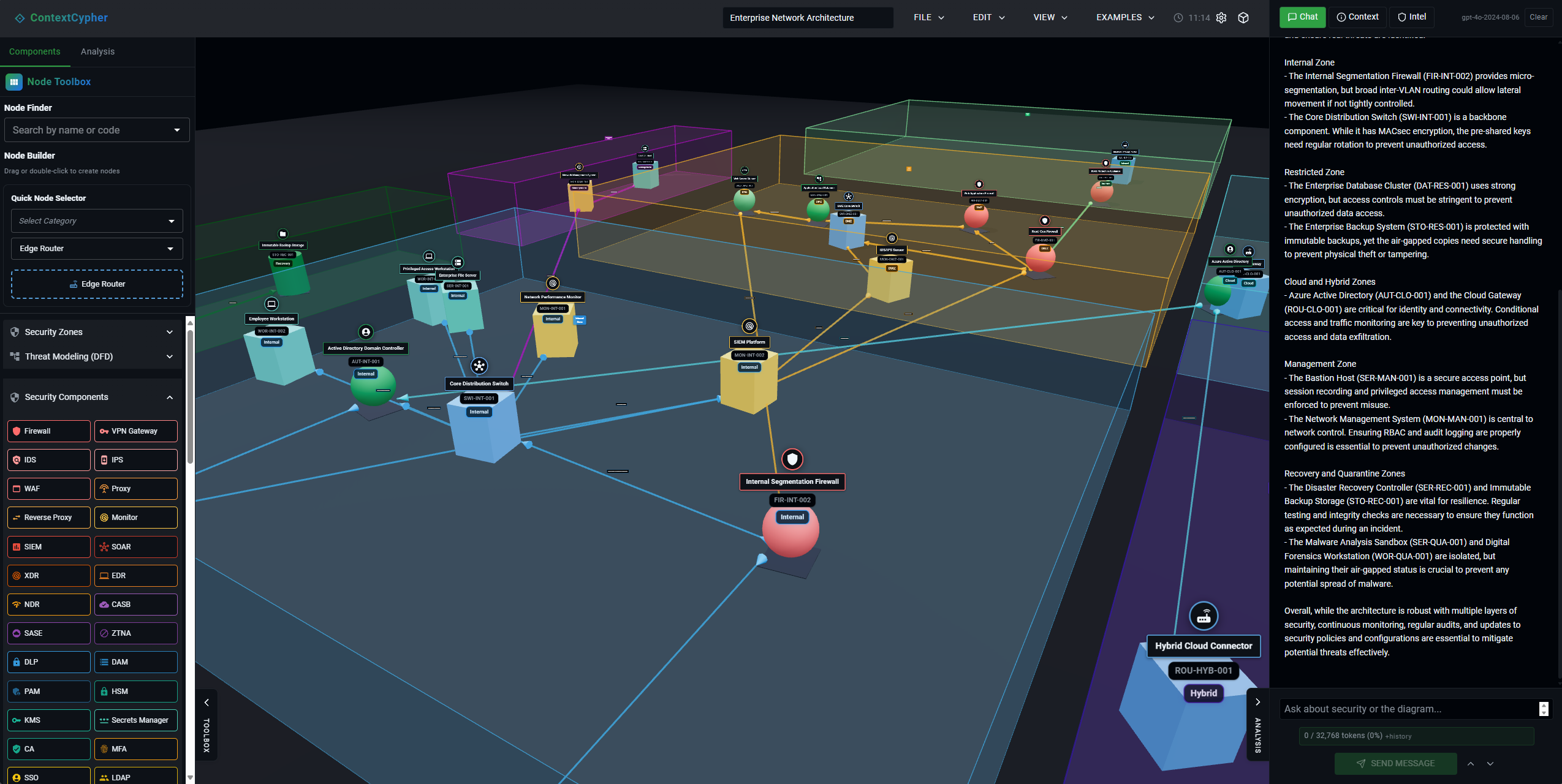
Click to enlarge
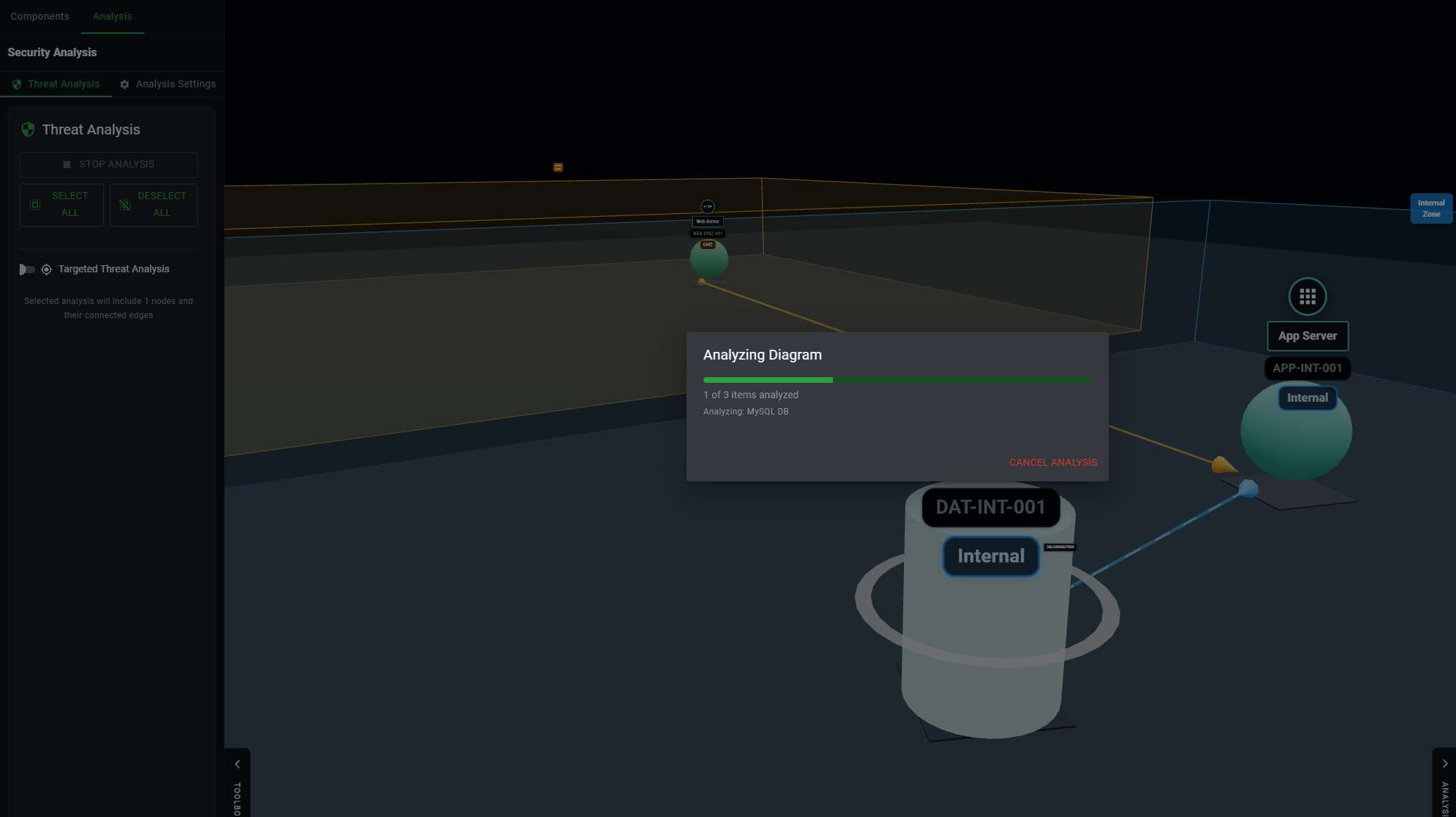
Step 4: Deep Threat Analysis
Beyond conversational analysis, you can trigger comprehensive threat assessments that leverage security frameworks and threat intelligence.
Automated Threat Identification
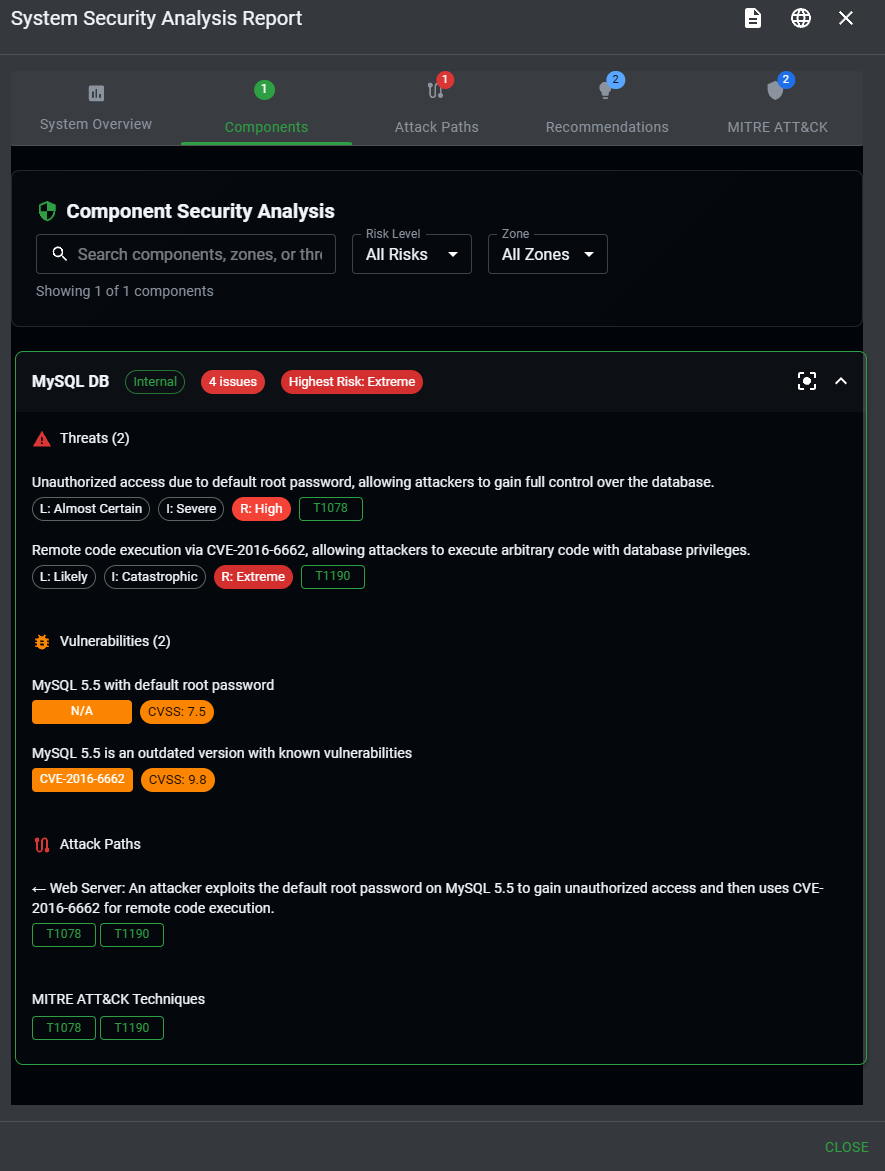
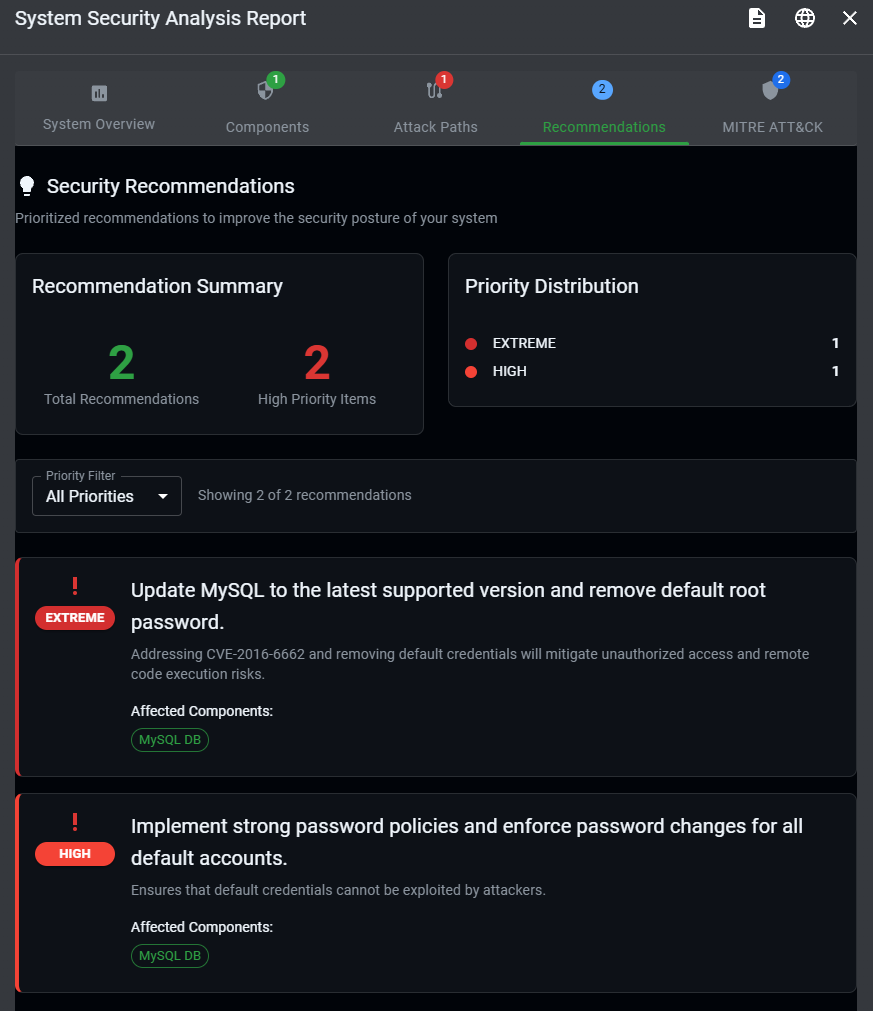
Click the "Analyze Threats" button to generate a complete security assessment that includes:
- Identified vulnerabilities for each component
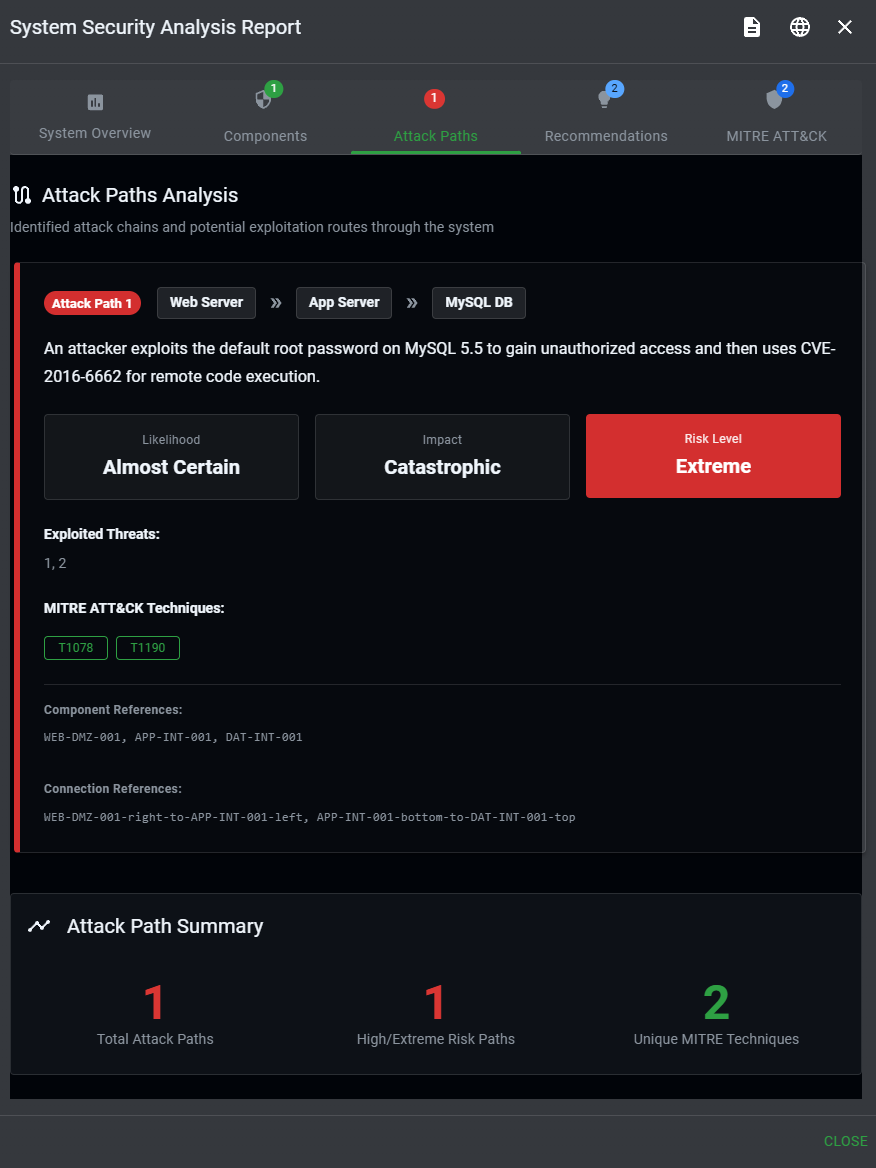
- Potential attack paths through your system
- Risk ratings based on likelihood and impact
- Specific TTPs (Tactics, Techniques, and Procedures) attackers might use
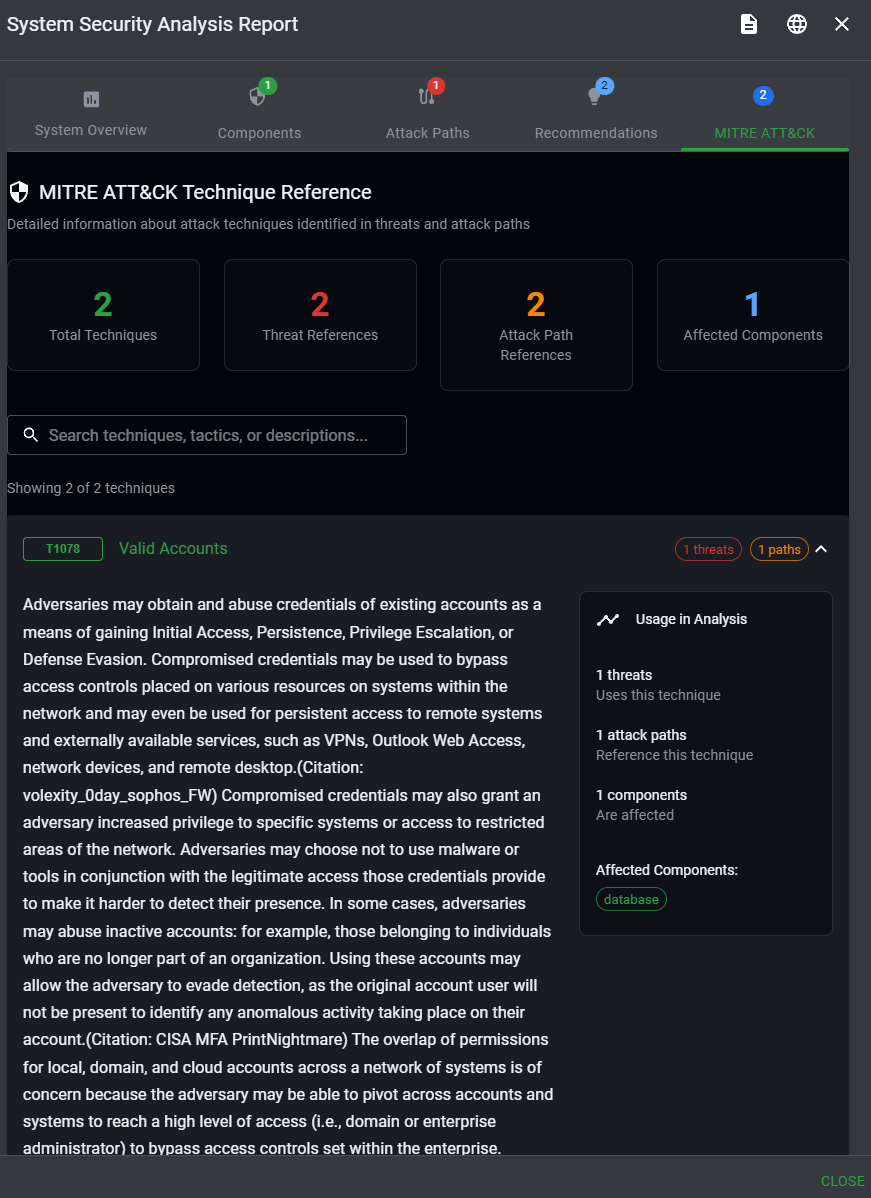
MITRE ATT&CK Mapping
The analysis maps identified threats to the MITRE ATT&CK framework, providing:
- Specific technique IDs (e.g., T1190 - Exploit Public-Facing Application)
- Tactic categories (Initial Access, Execution, Persistence, etc.)
- Real-world examples of how these techniques are used
- Detection and mitigation recommendations
Click to enlarge

Click to enlarge
Click to enlarge
Click to enlarge
Click to enlarge
Click to enlarge
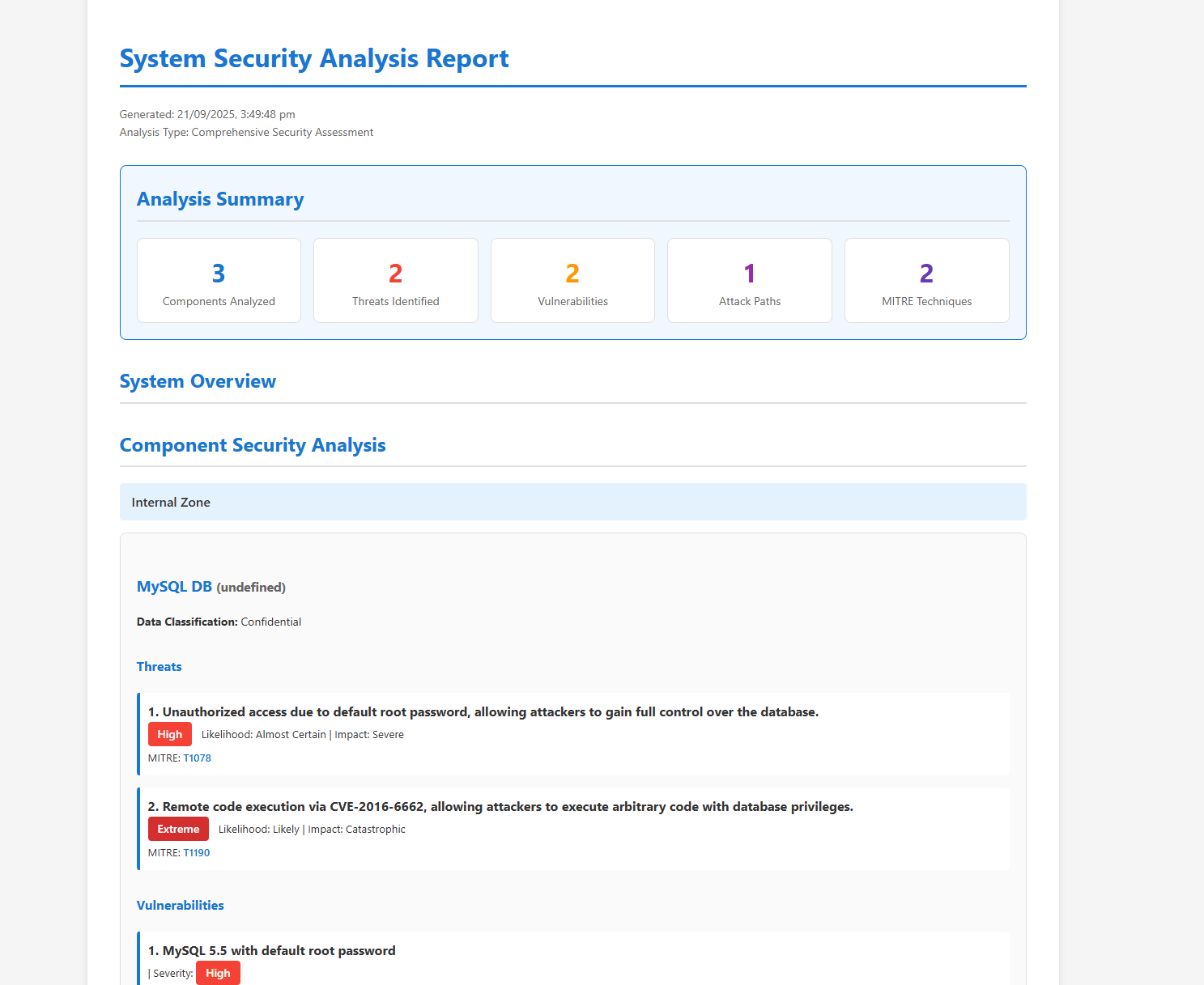
Professional Report Generation
Export your analysis as professional reports suitable for:
- Executive briefings with risk summaries
- Technical documentation with detailed findings
- Compliance audits with framework mappings
- Development teams with actionable remediation steps
Click to enlarge
The Human-AI Partnership
Throughout this workflow, the AI serves as a knowledgeable assistant that:
- Helps identify common vulnerabilities and attack patterns more consistently
- Provides consistent analysis based on security best practices
- Offers detailed technical knowledge on demand
- Scales to analyze complex architectures quickly
However, human expertise remains crucial for:
- Understanding business context and acceptable risk levels
- Prioritizing remediation based on available resources
- Designing practical security controls that don't impede operations
- Adapting generic recommendations to specific environments
Practical Workflow Example
Let me walk through a real scenario. Imagine you're tasked with threat modeling a microservices architecture. Here's how the AI-assisted workflow helps:
Scenario: E-commerce Platform Security Review
1. Import existing architecture (2 minutes)
Import your AWS architecture diagram from DrawIO, automatically converting VPCs, security groups, and services into threat model components.
2. Initial AI conversation (5 minutes)
Ask: "What are the critical data flows I should protect?" The AI identifies payment processing, user authentication, and inventory management as key flows.
3. Switch to 3D view to visualize layers
See your frontend, API gateway, microservices, and data stores in distinct layers, making security boundaries immediately apparent.
4. Run automated threat analysis
AI identifies 23 potential vulnerabilities, maps them to MITRE ATT&CK techniques, and prioritizes based on your architecture's exposure.
5. Generate executive report
Export a comprehensive report with risk ratings, attack paths, and specific remediation recommendations for your DevOps team.
Total time: 30 minutes for what traditionally takes 2-3 hours
Key Takeaways for Security Professionals
After working with AI-powered threat modeling, here's what stands out:
What AI Does Well
- Comprehensive coverage: Systematically checks for known vulnerabilities
- Technical depth: Provides detailed attack techniques on demand
- Speed: Analyzes complex architectures in minutes
- Consistency: Applies the same thorough approach every time
- Knowledge base: Incorporates latest security research and frameworks
Where Human Expertise Shines
- Business context: Understanding which risks actually matter to your organization
- Creative thinking: Identifying novel attack vectors specific to your environment
- Practical judgment: Balancing security with operational requirements
- Stakeholder communication: Translating technical risks into business impact
- Implementation expertise: Knowing what mitigations will actually work in your environment
Conclusion: A Practical Tool for Real Security Work
AI doesn't replace the need for skilled security professionals. Instead, it acts as a force multiplier – handling the repetitive analysis, ensuring comprehensive coverage, and providing deep technical knowledge on demand. This frees security teams to focus on what humans do best: understanding context, making judgments, and implementing practical solutions.
The key is viewing AI as a knowledgeable assistant rather than a magic solution. When given clear context and used as part of a structured workflow, AI significantly enhances both the speed and quality of threat modeling. And yes, it can help automate many aspects of the process – just not in the way many people initially imagine.
Getting Started
If you're interested in trying AI-powered threat modeling, ContextCypher is available as alocally installed web app via npmor online. It's free for personal and educational use with all features included — AI diagram generation, 3D visualization, MITRE ATT&CK mapping, automated reports, and more.
Important: AI-generated threat modeling is designed to augment human expertise, not replace it. All findings should be validated by qualified security professionals. For detailed information about capabilities and limitations, please review our Terms of Service.